Amazon has disrupted a targeted Russian hacking operation by the infamous APT29 group that exploited Microsoft’s device code authentication process. This news is critical for market stakeholders concerned with digital asset integrity and cloud platform security, as it showcases both the sophistication of adversary tactics and the necessity for proactive, fast-moving threat mitigation strategies.
Amazon’s Chief Information Security Officer, CJ Moses, confirmed that the scale of the recent cyberattack was narrower than many feared. He stated that only 10% of visitors to the compromised website were actually redirected to domains controlled by the threat actors. This figure highlights that while the breach was serious, the majority of users were not funneled into the malicious infrastructure.
Moses emphasized that Amazon’s security teams acted quickly to contain the situation and protect affected systems. The disclosure underscores both the sophistication of the attack and the importance of rapid defensive measures in reducing exposure. By keeping the number of redirected users limited, the impact of the incident was significantly constrained compared to what could have occurred if the attackers had maintained longer control.
Who are APT29 hackers?
APT29, also known as Cozy Bear, Midnight Blizzard, and several other aliases, operates under the Russian Foreign Intelligence Service (SVR). This group has repeatedly made headlines for attacks on Western governments, universities, and high-profile corporations, recently being linked to credential theft campaigns targeting Microsoft 365 through deceptive device authentication flows.
Technical attack details
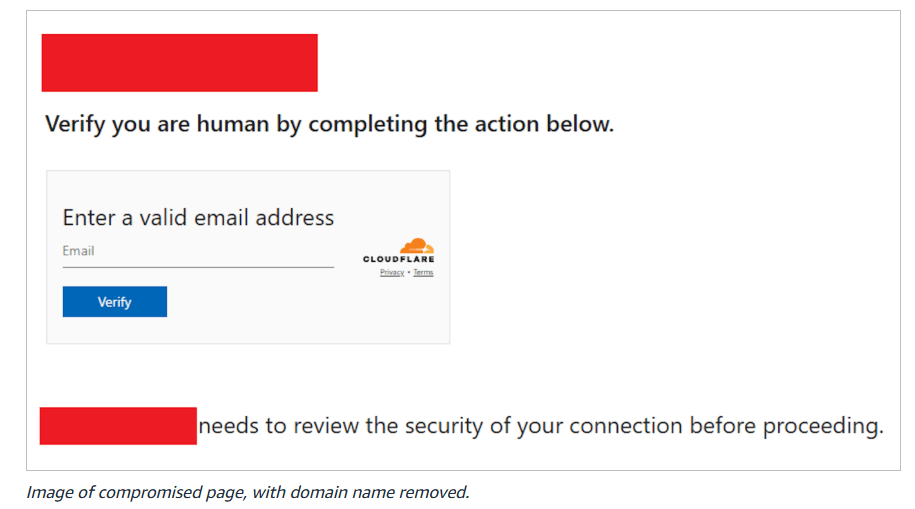
The June 2025 campaign relied on watering hole tactics: APT29 compromised legitimate websites and injected hidden JavaScript to quietly redirect around 10 percent of visitors to actor-controlled domains. Fake verification pages, designed to mimic Cloudflare, were used to trick users into entering legitimate Microsoft device codes. This step gave the hackers access to Microsoft accounts, with the aim of harvesting credentials and confidential data. Intricacies included base64 encoding to conceal code and cookies for evasion, preventing repeated redirects for the same user.
Analysis of the malicious code used by APT29 showed several evasion tactics that enabled the group to operate under the radar for some time. These included randomizing the redirection so that only about 10 percent of website visitors were targeted, which minimized the chances of rapid discovery and broad suspicion.
(source: aws.amazon.com)
Code Evasion Techniques
- Randomized Redirects: The scripts injected into compromised sites would selectively redirect only a small, random subset of visitors to attacker-controlled domains designed to look legitimate. This approach helped the operation stay undetected by limiting the exposure of the attack to security systems and users.
- Obfuscation Using Base64: Malicious scripts were hidden behind base64 encoding, making it harder for basic static analysis tools and security personnel to spot harmful intent. Only decoded analysis would uncover the real payload, raising the technical bar for defenders.
- Cookie Tracking: To avoid repeated redirection and alerting users – cookies were set for visitors who had already been redirected. This meant each person typically saw the attack page only once, further minimizing the chance of broad awareness and forensic detection.
- Infrastructure Pivoting: When Amazon blocked APT29’s domains or isolated compromised servers, the attackers quickly moved operations to new hosting providers and registered fresh domains. This flexibility kept their campaign alive and shows the benefit for defenders in cooperating rapidly and maintaining monitoring even after initial disruption.
Amazon’s detection and disruption process
Amazon’s threat intelligence team built dedicated analytics to identify the malicious APT29 infrastructure. Once discovered, Amazon partnered with Cloudflare and Microsoft, quickly isolating compromised EC2 instances and neutralizing the attacker’s domains. Even as hackers rushed to switch infrastructure providers and registered new domains such as cloudflare.redirectpartners[.]com, Amazon tracked and foiled each pivot, demonstrating rapid adaptability in cybersecurity defense.
Industry-wide coordination
The incident highlights the critical role of cross-industry collaboration. Amazon informed Microsoft and coordinated with other cloud and security vendors to track and close APT29’s operations. The company’s transparency and shared intelligence accelerated defensive responses and public awareness regarding advanced persistent threats.
Market implications and recommendations
For market leaders and cybersecurity managers, the incident is a warning about rising attack sophistication targeting device-based authentication flows. There is a need for continuous vigilance, regular code audits, and swift sharing of threat intelligence between cloud providers, application vendors, and enterprise IT teams. Organizations should urgently review authentication procedures and invest in high-fidelity monitoring of credential-related traffic to minimize risk exposure.
Guidance for End Users
- Vigilance for redirects: Stay alert for suspicious redirects, especially ones that look like security verification pages. APT29 attackers often create realistic pages to trick users into revealing credentials or approving new devices.
- Authentication requests: Always check carefully before authorizing any device code or account access. Confirm requests are genuine, matching with known procedures of Microsoft or the intended provider.
- Multi-factor authentication (MFA): Activate MFA for every account. AWS now requires MFA for root accounts, highlighting its importance as a basic defense against unauthorized access.
- Avoid copy-paste requests: Be cautious if a page asks to copy and run commands, especially in Windows’ Run dialog (Win+R). This tactic, dubbed “ClickFix,” manipulates end users into running harmful code themselves.
Advice for IT Administrators
- Device authentication policies: Follow Microsoft’s security guidance on device authentication flows. If these features are not necessary, disable them to remove the attack vector.
- Conditional access: Limit device authentication by enforcing location, compliance, and risk-based conditions. Ensure authentication attempts from risky contexts are flagged or blocked.
- Logging and monitoring: Closely track authentication events, especially for new device authorizations. Monitor for unusual activity patterns or frequent requests from unfamiliar locations.
Indicators of Compromise (IOCs)
Pay close attention to these domains in threat intelligence monitoring:
- findcloudflare[.]com
- cloudflare[.]redirectpartners[.]com
Review decoded JavaScript if found, and check for unusual domains embedded in redirect code. Remove and investigate any traffic or code referencing these indicators to thwart ongoing campaigns.

(Image Credit – Amazon AWS)

